TIPTOP Identity and access management (IAM)
TipTop Platform IAM solutions for Application, Users, Employee , Customer , Devices and Business Users with advanced 5th generation Identity and Access Management
TipTop Platform Identity and Access Management systems and services provide new technical capabilities for organizations to unify their entire identity and access management requirement may it be Applications or Physical access using IOT devices .
Implementing TipTop Identity’s solutions for IAM can provide Secured and Robust IAM environment with better user experiences and integrated Multidimensional organization chart and AHALTS validation with advanced Biometrics that include Face recognition and finger Print validation beside conventional multifactor Authentication services. The system gives a ready organizational IT unification framework with Lowest cost of ownership.
TipTop Planet is a IAM integrated Application Development Platform which is designed to adapt to need of Humans, Machines, Applications , Devices and Humanoids with advanced Identity and access management
Our Platform includes Framework of processes, policies and technologies that facilitates the management of Human, electronic , digital or Machines identities.
The platform Controls user access to critical information and Devices within the organizations. It Includes single sign-on systems, two-factor authentication, multi-factor authentication and privileged access management .
The Platform has advanced Ability to securely store identity and profile data as well as data governance functions to ensure that only data that is necessary and relevant is shared
IAM for MTM (Machine to Machine)communication)Manage identity and access for cloud admin, app developers, and users

IAM Platform services
Application Management
with Application Management every application is provided a Application Identity Key that helps developers to get access to other services of the platform based on the access permissions of the users or applications as the platform allows user to application , device to application and application communication this is a great feature for AI based services that work in back end
Object Management
with Object management service every resource is converted into object allowing permission and grouping based on objects this is a micro concept against legacy resource permission methods that required a much larger control and complex coding when it would come to granular permission whereas our platform allows creating a object and applying roles and permission on that
User Management
The main goal of User identity and access Management is to identify the right users by using the correct credentials to access the right resource for the appropriate purpose. Identity and access involve describing and handling the roles alongside the access privileges. Access is granted or denied based on the roles and scenarios that an individual is entitled to. After the identity is established, it can then be managed, modified, or removed based on the circumstances over the lifetime of the identity.
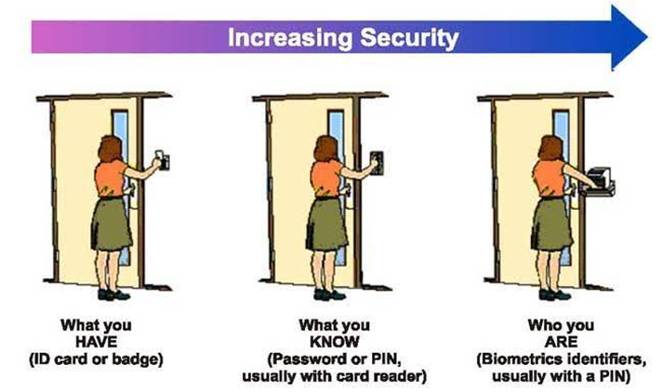
with our cloud identity service every user account is given a unique identity which becomes the identity for all the application and also the user is provided a password . Our AHALTS platform is integrated into this IM identity and extends all Biometric identification features like finger scan, retina scan, face recognition, OTP etc.
Privilege Access Management
TTP PAM Safeguards employees with elevated rights
Secure, control and monitor access to an organization’s critical information and resources.
Shared access password management, privileged session management, vendor privileged access management and application access management.
lower the risk of admin credentials being stolen or misused.
Machine to Machine
M2M connectivity is a need of the day as future technology has to be Internet of Things (IoT ) Ready.
Today with the fast introduction of IIOT concept related to Industry 4.0 it is becoming increasingly important for having a IAM Platform that has Machine to Machine communication.
Our machine to machine technology that allows two registered devices have a individual identity and can exchange information with each other, for example a AI driven BOT wants to send a command to a Robot or a IOT switch this requires a robust security to ensure that only authenticated devices only can communicate and send data to each other . This communication that occurs between the machines or devices is autonomous, there is no need for human intervention for this data exchange to take place.
SSO
Single Sign-on (SSO) allows users to log in to one application and is then signed in to other applications automatically The user signs in only one time, hence the name of the feature (Single Sign-on).. Our SSO provides a seamless experience for users when using your applications and services. Instead of having to remember separate sets of credentials for each application or service, users can simply log in once and access their group of applications.
Our Authentication provider with a simple SDK handles the entire authentication process redirecting the first login to our universal authentication Domain and this returns a token that is used for accessing across multiple applications
Bio-metric Authentication
Our platform has a very Robust Human identification service that uses various methods based on user need these include Finger print , Retina Scan, Vein scan, Voice and remote live person manual verification
Face Id
Our Face recognition cloud services are one of the most accurate AI algorithm with 99.8% accuracy the UserID is mapped to the FaceID using a KYC registration and subsequently this service is the most advanced authentication service that enables multi-factor authentication with user real time photo the face server has anti spoofing feature that eliminates proxy identity. please see AHALTS.com for detailed info
API Management
TipTop Platform has a flexible API server that has a library of ready to use API required for building applications with advanced business requirements and these libraries are getting more and more features with hundreds of API adding every few months
